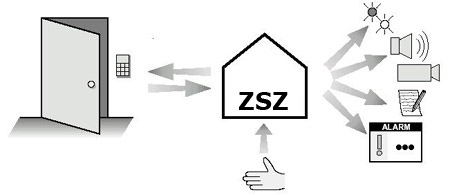
a) Access control system and door status:
- User identification and response in accordance with the rights assigned to him,
- Automatic system reaction to specific events, e.g. door open – turn on the light (if it is dark enough), music, no access – send a message through the sound system to this zone, etc.,
- Checking the door status: door open, open for too long, not open despite permit, balanced (alarm!),
- Granting access to specific rooms or places on demand after prior approval by the operator,
- Remote (from a PC) opening of doors, gates, etc. by the system operator,
- Recording in the database of all events related to controllers with the date, time, identifier number, system response, etc.,
- Event reporting (single controller, group of controllers).
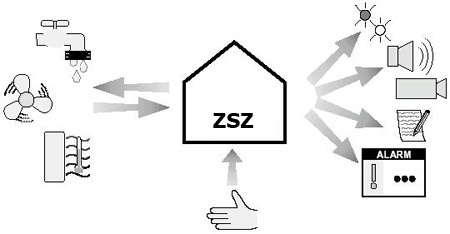
b) Controlling the supply of utilities (electricity, water, heating, etc.) and their metering.
- Control of ventilation or air conditioning devices or systems.
- Cooperation with sensors and measuring devices,
- Cooperation with executive devices,
- Full visualization of current states of sensors and devices on synoptic maps on monitors, command and operator stations,
- Work in automatic mode (time, conditional or time-conditional) with the possibility of taking control of executive devices by the operator at any time,
- Work in the mode of manual control of executive devices by the operator,
- Work in emergency mode in emergency situations with notification of relevant services,
- Recording of all events in the system (change of sensor states, switching on / off of actuators, operator decisions with operator identification and exact time of event occurrence, etc.).
c) Cooperation with the internal communication system (intercom and radio node)
- Communication between the talk and operator panel with the option of registering the date and time of the conversation,
- Possibility to connect to the local telephone exchange and switch calls from this exchange to the conversation panel and from the conversation panel to the telephone exchange,
- Possibility to control conducted conversations and their registration,
- The ability to display the image of the caller in the case of cooperation with the CCTV system,
- The possibility of organizing the so-called visit rooms with display and recording of visit time.

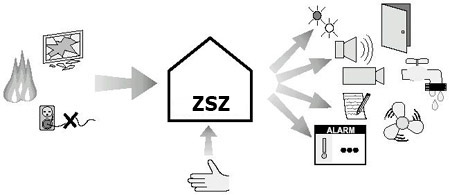
d) Alarm, fire, attack, etc. systems:
The alarm system is activated in emergency situations such as: fire, burglary, lack of power, etc. It is designed not only to increase the reaction speed to an event by automatically executing the commands defined in the system, but also to reduce the possibility of operator error in a stressful situation.
Alarm system tasks:
- Signaling of alarm events on site and their interpretation, with particular regard to the place and type of event,
- Automatic system reaction, e.g. alarm activation, door lock, camera view of the event location,
- The operator has to confirm the fact of an emergency by accepting the message. The confirmation with the operator’s code is saved in the event database,
- Allowing the operator to take more extensive action than in an non-emergency situation, e.g. blocking access to all rooms (burglary), opening all doors (fire), etc.
- Audible and visual alarm signaling – each type of alarm triggers a different voice message and is displayed on the monitor screen.
- The message clearly indicates the reason for its occurrence,
- Direct or indirect (through dedicated control panels) cooperation with any sensors and attack buttons,
- Direct or indirect (through dedicated control panels) cooperation with radio links for wireless panic buttons,
- Cooperation with any control panels of alarm, fire, signaling, etc. systems.
- Remote control of their work.
- Monitoring and visualization of the work of these exchanges and integration of local systems as part of a common monitoring, management and security system in the facility.
e) Fence surveillance and perimeter security system
- Direct or indirect (through dedicated control panels or intermediaries) cooperation with any detectors, perimeter protection barriers (microwave, infrared, laser, etc.), sensor cables and all devices for perimeter protection,
- Zoning,
- Control of individual zone violations and automatic reaction to an event depending on the zone number, e.g. switching on external lighting, viewing from a camera, activation of an additional protection system or notification, etc.,
- Voice and visual messages about a fence violation, including the area of the violation at the operator’s position.
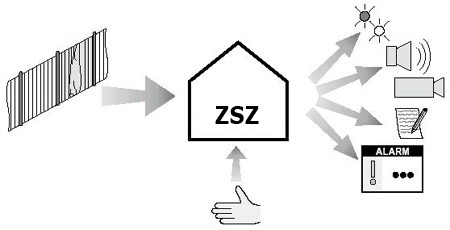
f) Cooperation with the metal detection system
Metal detectors are primarily used to control people entering the facility.
The cooperation system ensures:
Independent work of the metal detector with notification of the operator about the alarm and automatic response to the alarm event by the IMS, e.g. bypassing the input, recording in the alarm mode by the television surveillance system, etc.,
The operator takes control of the detector from the moment the alarm is triggered until the operator confirms it. An alarm event is automatically saved to the event database along with the confirmation operator code (for disabling the alarm).
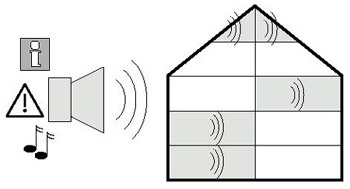
g) Emergency sound system
The sound system enables the distribution of voice messages in emergency situations.
System Features:
- Division of the object into zones,
- Automatic distribution of system alarm messages to a given zone in emergency situations, e.g. fire, etc.,
- Distribution of messages from operator positions,
- Distribution of information messages,
- Using the sound system as a paging system,
- Daily use as a music distribution system.
h) Cooperation with the television supervision system
In the event of an alarm event, the operator on the screen of the monitor not only sees a dry message about its occurrence, but using a preview from a given camera can perfectly assess the degree of danger and take appropriate action. The observation system can also be used as an additional protection for particularly sensitive points of the object, e.g. vault, server room, etc. The operator sees on the monitor screen not only information about the access request, along with a photo of the identifier user, but also the face of the person who actually brought the card closer to the reader.
System features:
- Remote switching on and displaying on the monitor screen of an image from a specific camera of a television surveillance system,
- Automatic switching of video recording devices from the frame-by-frame mode to the continuous mode of the image from the selected camera in the event of an alarm event,
- Possibility of the IMS operator to take full control over the television surveillance system devices.
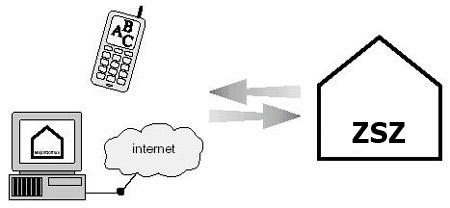
i) Cooperation with a mobile phone, internet, fax
Used primarily in emergency situations to notify people outside the facility of the situation and creates the possibility of taking certain, specific actions from their current location.
The system enables:
- Sending messages provided by subsystems to specific people via a mobile phone (SMS), e-mail, fax,
- Remote launch of specific system functions using a mobile phone (the phone’s SIM card must be defined in the system),
The presented subsystems only serve to show the flexibility of the system and the possibilities of adapting it to the specific requirements of the customer. Because the user can define the configuration of the IMS system at the level of basic components, there are no problems or restrictions as to the possibility of creating own subsystems. Although this requires a significant number of parameters to be defined, it is possible to build a “tailor-made” system, adapting it to the individual needs and conditions of a particular object